Lax Security Around URL Shortener Exposed PII Of US Retailer Carters Customer Base
US retailer Carter's accidentally exposed the personally identifiable information (PII) of potentially hundreds of thousands of customers.
On Friday, vpnMentor said the incident was not caused by an unsecured bucket or misconfiguration in a cloud storage system -- as is often the case with when it comes to accidental leaks -- but rather a "simple oversight" in the firm's online order tracking infrastructure.
The breach, discovered through a web mapping project underway at vpnMentor, was caused by a failure to implement authentication protocols for a popular URL shortener tool used on the retailer's US e-commerce domain.
Carter's is a major retailer for baby clothing and apparel in the United States which now operates worldwide. The company generated over $3 billion in revenue during 2020.
When a purchase was made through the Carter's US website, the vendor would automatically send them a shortened URL to access a purchase confirmation page. However, a lack of security around the URLs themselves, together with no authentication to verify the customer, was problematic.
The confirmation pages, generated by Linc's automation platform, contained a variety of customer PII -- and to add another potential problem, the links never expired, allowing anyone to access these pages at will, at any time, alongside backend JSON records.
Information exposed on these pages included full names, physical addresses, email addresses, phone numbers, shipping tracker IDs, as well as purchase and transaction details.
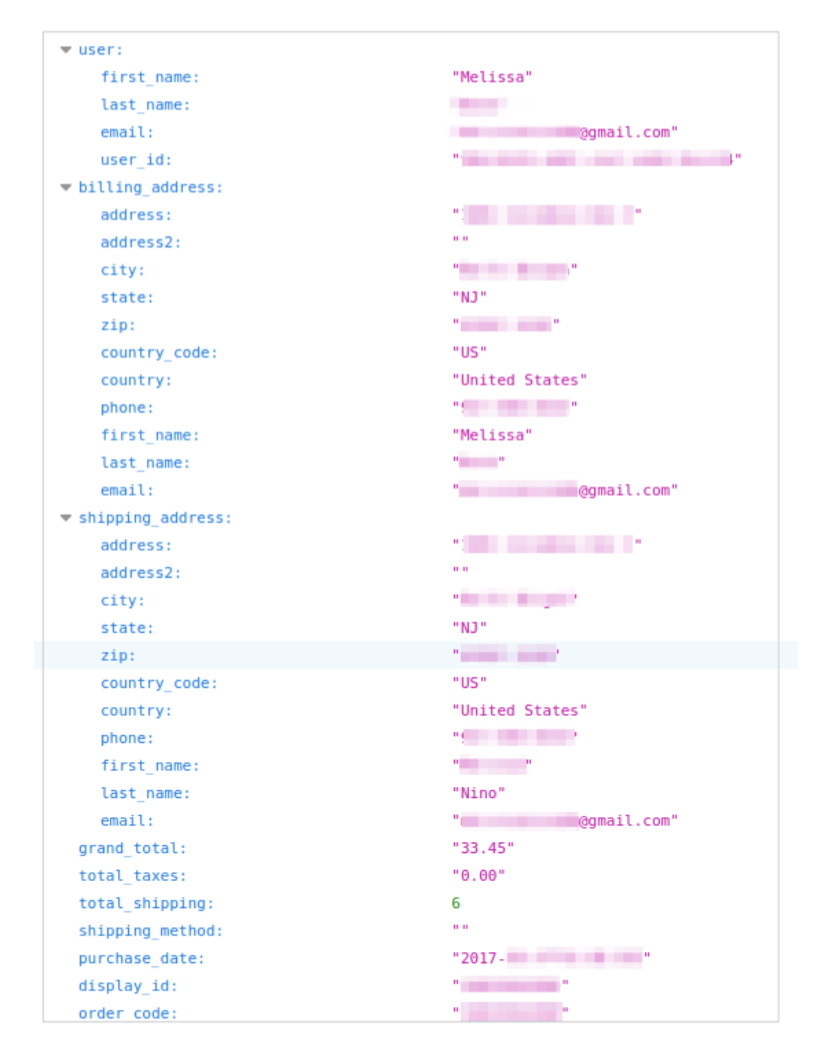
"Due to the massive volume of sales Carter's enjoys every year, this simple but drastic oversight exposed 100,000s of people to fraud, theft, and many other dangers," the researchers say.
Due to the nature of the flaw, the exact number of records exposed is unknown. However, the team estimates that over 410,000 records could have been open to abuse, with the potential impact including phishing, social engineering, and identity theft.
Carter's was informed of the security breach on March 22, five days after the initial discovery. Contact was made on March 30, and initially, the retailer asked vpnMentor to submit their findings through Bugcrowd. However, Carter's eventually accepted the direct report and the shortened URLs were pulled between April 4 - 7.
ZDNet has reached out to Carter's but has not heard back at the time of publication.
Previous and related coverage
- Data leak implicates over 200,000 people in Amazon fake product review scam
- Paleohacks data leak exposes customer records, password reset tokens
- 23,600 hacked databases have leaked from a defunct 'data breach index' site
Have a tip? Get in touch securely via WhatsApp | Signal at +447713 025 499, or over at Keybase: charlie0
Reassessing AI Investments: What The Correction In US Megacap Tech Stocks Signals
The recent correction in US megacap tech stocks, including giants like Nvidia, Tesla, Meta, and Alphabet, has sent rippl... Read more
AI Hype Meets Reality: Assessing The Impact Of Stock Declines On Future Tech Investments
Recent declines in the stock prices of major tech companies such as Nvidia, Tesla, Meta, and Alphabet have highlighted a... Read more
Technology Sector Fuels U.S. Economic Growth In Q2
The technology sector played a pivotal role in accelerating America's economic growth in the second quarter of 2024.The ... Read more
Tech Start-Ups Advised To Guard Against Foreign Investment Risks
The US National Counterintelligence and Security Center (NCSC) has advised American tech start-ups to be wary of foreign... Read more
Global IT Outage Threatens To Cost Insurers Billions
Largest disruption since 2017’s NotPetya malware attack highlights vulnerabilities.A recent global IT outage has cause... Read more
Global IT Outage Disrupts Airlines, Financial Services, And Media Groups
On Friday morning, a major IT outage caused widespread disruption across various sectors, including airlines, financial ... Read more

