A Deep Dive Into The Operations Of The LockBit Ransomware Group
Researchers have provided an in-depth look at how LockBit, one of the newer ransomware groups on the scene, operates.
Ransomware has become one of the most disruptive forms of cyberattack this year. It was back in 2017 with the global WannaCry outbreak that we first saw the severe disruption the malware could cause, and in 2021, nothing seems to have changed for the better.
This year alone, so far we've seen the Colonial Pipeline ransomware disaster that caused fuel supply shortages across parts of the US; ongoing issues at Ireland's national health service, and systematic disruption for meat processor giant JBS due to the malware.
Ransomware operators will deploy malware able to encrypt and lock systems, and they may also steal confidential data during an attack. Payment is then demanded in return for a decryption key.
Losing money by the second while their systems fail to respond, victim enterprise players may then be subject to a second salvo designed to pile on the pressure -- the threat of corporate data being either leaked or sold online through so-called leak sites in the dark web.
Ransomware attacks are projected to cost $265 billion worldwide by 2031, according to Cybersecurity Ventures, and payouts now commonly reach millions of dollars -- such as in the case of JBS. However, there is no guarantee that decryption keys are fit for purpose or that paying once means that an organization will not be hit again.
A Cybereason survey released this week suggested that up to 80% of businesses who fell prey to ransomware and paid up have experienced a second attack -- potentially by the same threat actors.
The threat of ransomware to businesses and critical utilities has become serious enough that the issue was raised during a meeting between US President Joe Biden and Russian President Vladimir Putin at the Geneva summit.
Each group has a different modus operandi and ransomware operators are constantly 'retiring' or joining the fold, often through a Ransomware-as-a-Service (RaaS) affiliate model.
On Friday, the Prodaft Threat Intelligence (PTI) team published a report (.PDF) exploring LockBit and its affiliates.
According to the research, LockBit, believed to have previously operated under the name ABCD, operates a RaaS structure that provides affiliate groups a central control panel to create new LockBit samples, manage their victims, publish blog posts, and also pull up statistics concerning the success -- or failure -- of their attack attempts.
The investigation revealed that LockBit affiliates most often will buy Remote Desktop Protocol (RDP) access to servers as an initial attack vector, although they may also use typical phishing and credential stuffing techniques.
"Those kinds of tailored access services can be purchased as low as $5, thus mak[ing] this approach very lucrative for affiliates," Prodaft notes.
Exploits, too, are used to compromise vulnerable systems, including Fortinet VPN vulnerabilities that have not been patched on target machines.
Forensic investigations of machines attacked by LockBit affiliates show that threat groups will often first try to identify "mission-critical" systems including NAS devices, backup servers, and domain controllers. Data exfiltration then begins and packages are usually uploaded to services including MEGA's cloud storage platform.
A LockBit sample is then deployed manually and files are encrypted with a generated AES key. Backups are deleted and the system wallpaper is changed to a ransom note containing a link to a .onion website address to purchase decryption software.
The website also offers a decryption 'trial,' in which one file -- with a size smaller than 256KB -- can be decrypted for free.
However, this isn't just to show that decryption is possible. An encrypted file needs to be submitted for affiliates to generate a decryptor for that particular victim.
If victims reach out, attackers can open a chat window in the LockBit panel to talk to them. Conversations will often start with the ransom demand, payment deadline, method -- usually in Bitcoin (BTC) -- and instructions on how to purchase cryptocurrency.
Prodaft was able to obtain access to the LockBit panel, revealing affiliate usernames, the number of victims, registration dates, and contact details.
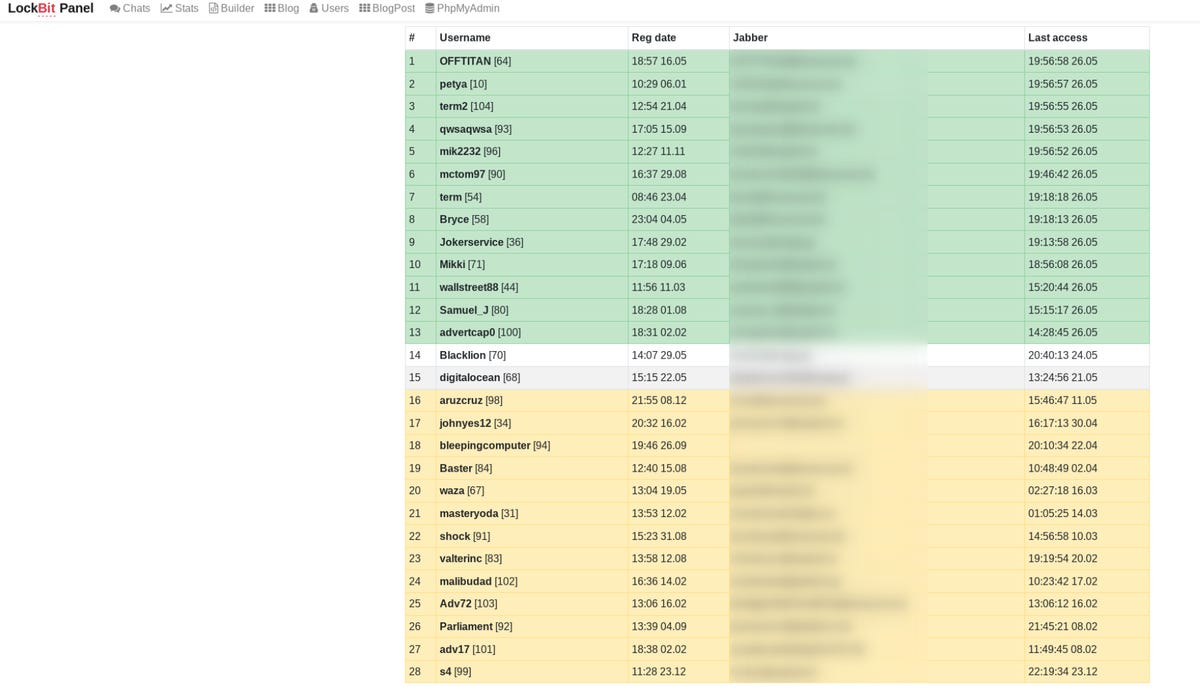
The research team says that clues within the affiliate names and addresses suggest that some may also be signed up with Babuk and REvil, two other RaaS groups -- however, the investigation is ongoing.
On average, LockBit affiliates request roughly $85,000 from each victim, 10 - 30% of which goes to the RaaS operators, and the ransomware has infected thousands of devices worldwide. Over 20% of victims on the dashboard were in the software and services sector.
"Commercial and professional services as well as the transportation sector also highly targeted by the LockBit group," Prodaft says. "However, it should be noted that the value of the ransom is determined by the affiliate after various checks using online services. This value does not solely depend on the sector of the victim."
At the time of writing, LockBit's leak site was unavailable. After infiltrating LockBit's systems, the researchers decrypted all of the accessible victims on the platform.
Earlier this month, Bleeping Computer reported that LockBit was a new entrant to a ransomware cartel overseen by Maze. Prodaft told ZDNet that as they "detected several LockBit affiliates are also working for other ransomware groups, collaboration is very likely."
Previous and related coverage
- Biden and Putin spar over cybersecurity, ransomware at Geneva summit
- Most firms face second ransomware attack after paying off first
- Ransomware is the top cybersecurity threat we face, warns cyber chief
Have a tip? Get in touch securely via WhatsApp | Signal at +447713 025 499, or over at Keybase: charlie0
Reassessing AI Investments: What The Correction In US Megacap Tech Stocks Signals
The recent correction in US megacap tech stocks, including giants like Nvidia, Tesla, Meta, and Alphabet, has sent rippl... Read more
AI Hype Meets Reality: Assessing The Impact Of Stock Declines On Future Tech Investments
Recent declines in the stock prices of major tech companies such as Nvidia, Tesla, Meta, and Alphabet have highlighted a... Read more
Technology Sector Fuels U.S. Economic Growth In Q2
The technology sector played a pivotal role in accelerating America's economic growth in the second quarter of 2024.The ... Read more
Tech Start-Ups Advised To Guard Against Foreign Investment Risks
The US National Counterintelligence and Security Center (NCSC) has advised American tech start-ups to be wary of foreign... Read more
Global IT Outage Threatens To Cost Insurers Billions
Largest disruption since 2017’s NotPetya malware attack highlights vulnerabilities.A recent global IT outage has cause... Read more
Global IT Outage Disrupts Airlines, Financial Services, And Media Groups
On Friday morning, a major IT outage caused widespread disruption across various sectors, including airlines, financial ... Read more

