Crypto investigator ZachXBT tweeted evidence of a network of 21 North Korea crypto developers that make $500K a month working for “established crypto projects.”
ZachXBT tweeted on August 15 that he believes a “single entity in Asia,” probably working out of North Korea, is receiving $300,000 to $500,000 per month. This entity has at least 21 employers for over 25 crypto projects.
1/ Recently a team reached out to me for assistance after $1.3M was stolen from the treasury after malicious code had been pushed.
Unbeknownst to the team they had hired multiple DPRK IT workers as devs who were using fake identities.
I then uncovered 25+ crypto projects with… pic.twitter.com/W7SgY97Rd8
— ZachXBT (@zachxbt) August 15, 2024
ZachXBT claims that the DPRK workers recently stole $1.3 Million which was actually laundered via a series of transactions, including transferring to a theft address. Out of the stolen sum, 16.5 Ether ended up to two different exchange addresses.
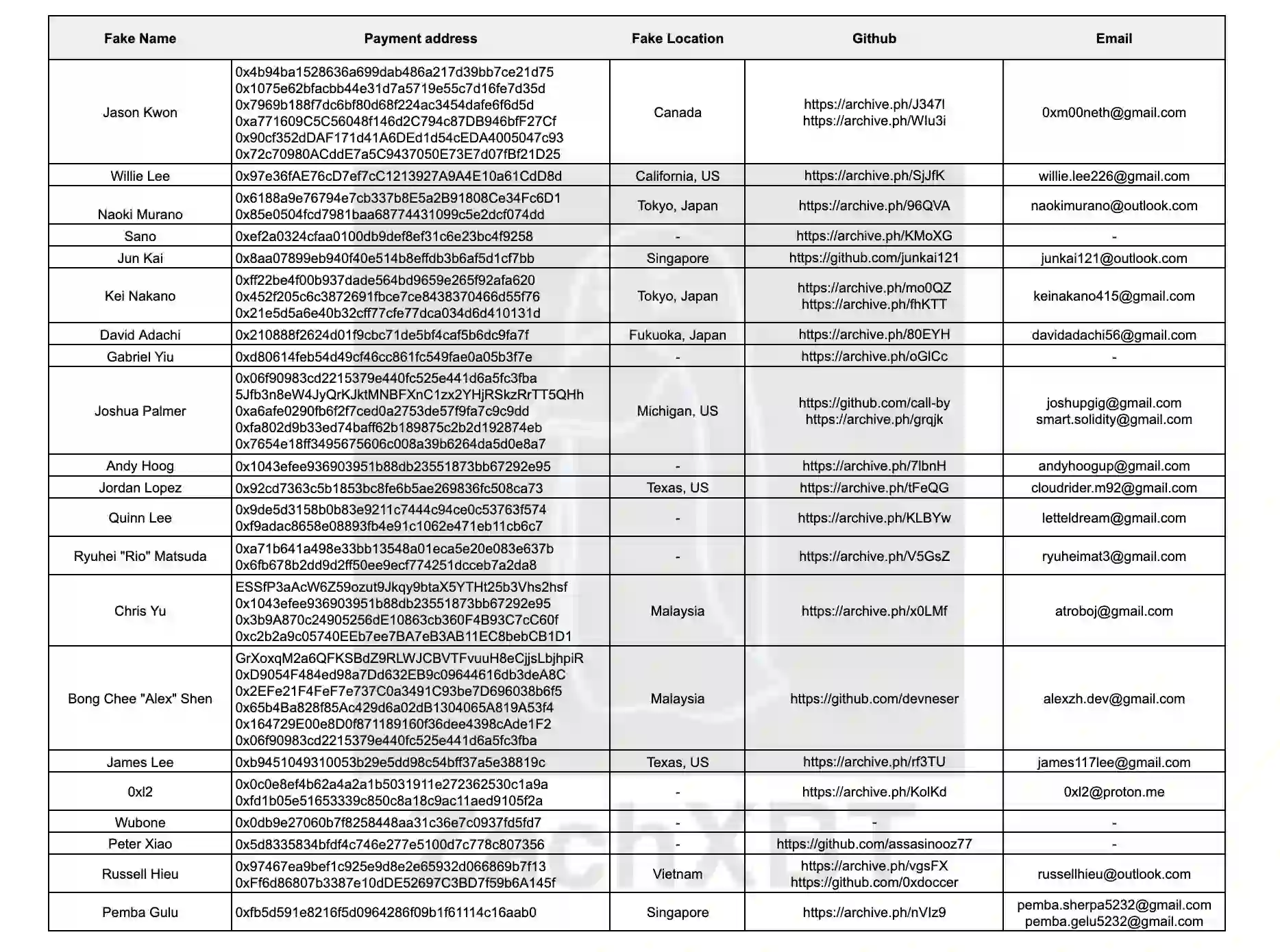
ZachXBT wrote, “Using multiple payment addresses for 21 devs I was able to map out a cluster with the most recent batch of payments for ~$375K over the last month. 0xb721adfc3d9fe01e9b3332183665a503447b1d35. In the past week you may have seen me tagging projects telling them to DM me.”
On doing intensive investigation, ZachXBT found a cluster of developers getting “$375,000 over the last month, and these payments were linked to IT workers in North Korea. Amongst them was an individual Sim Hyon Sop, who has been penalized by the Office of Foreign Assets Control (OFAC) for allegedly orchestrating financial transfers that support North Korea’s weapons programs.
Similarly, another OFAC-sanctioned individual, Sang Man Kim, who committed DPRK-related cybercrime in the past, has been linked to this particular entity.
ZachXBT made some revelations on this too, as he added, “Some funny moments from the investigation include:
– Russia Telecom IP overlap between devs supposedly in US and Malaysia.
-Recorded dev and they accidentally leaked their other identities on a notepad
-Dev payment addresses a few hops from Sang Man Kim and Sim Hyon Sop who are on the OFAC sanctions list
-Some devs were placed by recruitment companies
-Multiple projects with 3+ IT workers who referred to each other.”
After ZachXBT’s tweets came to light, another project found out they had hired one of the DPRK IT workers i.e., Naoki Muran who was listed by ZachXBT and shared his post in their chat. ZachBXT added that, immediately within two minutes, Naoki left the chat and wiped his GitHub.
Offlate, firms linked to the Democratic People’s Republic of Korea (DPRK) are infamously found to be the masterminds of a few cyber attacks and other scams. They are involved in cyber crimes including phishing, exploiting software flaws, cyber intrusions, private key exploits and in-person infiltration.
Also Read: ZachXBT Suspects Lazarus Group Link in $230M WazirX Hack


