Researchers Find Four New Malware Tools Created To Exploit Pulse Secure VPN Appliances
Researchers have uncovered four new malware families designed to target Pulse Secure VPN appliances.
Pulse Secure's virtual private network (VPN) and Secure Connect (PSC) solutions are used by corporations worldwide to provide secure access to business systems. However, on April 20, FireEye's Mandiant cyber forensics team disclosed attacks against defense, government, and financial organizations utilizing vulnerabilities in the software.
The major vulnerability at hand is CVE-2021-22893, issued a CVSS severity score of 10, described as an authentication bypass impacting Pulse Connect Secure permitting unauthenticated attackers to perform remote arbitrary code execution (RCE).
Other security flaws connected to attacks are CVE-2019-11510, CVE-2020-8260, and CVE-2020-8243, which can be used to establish persistence on a vulnerable appliance and further compromise devices.
Mandiant suspects that Chinese threat actors are exploiting the vulnerabilities, and now, intrusions have been detected at defense, government, technology, transport, and financial entities in the United States and Europe.
According to the researchers, UNC2630 and UNC2717 are the main advanced persistent threat (APT) groups involved in these attacks, and both of which "support key Chinese government priorities."
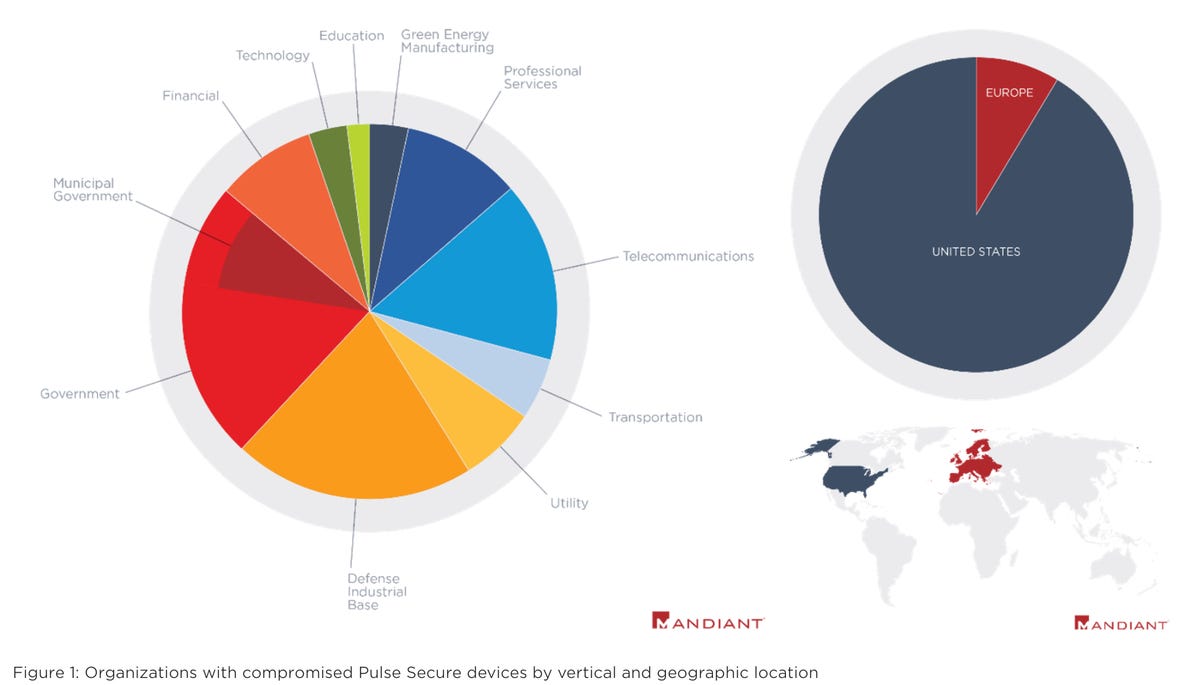
"Many compromised organizations operate in verticals and industries aligned with Beijing's strategic objectives outlined in China's recent 14th Five Year Plan," Mandiant says. "While there is evidence of data theft at many organizations, we have not directly observed the staging or exfiltration of any data by Chinese espionage actors that could be considered a violation of the Obama-Xi agreement."
In Mandiant's original report, 12 separate malware families and tools, including the Atrium and Slightpulse webshells, had been found that weaponized Pulse Secure vulnerabilities.
This number has now reached 16 with the discovery of four new malware families linked to UNC2630:
- Bloodmine: This utility parses PSC log files and extracts information relating to logins, message IDs, and web requests.
- Bloodbank: This malware is designed for credential theft and parses files containing password hashes or plaintext credentials.
- Cleanpulse: Cleanpulse is a memory patching tool for preventing specific log events. Mandiant discovered this malware in "close proximity" to an Atrium webshell.
- Rapidpulse: This is a webshell that exists as a modification to a legitimate Pulse Secure file and is not only capable of arbitrary file read, but can also act as an encrypted file downloader.
Mandiant notes that in some cases of intrusion, the Chinese threat actors removed a number of backdoors -- but left persistence patchers potentially as a means to regain access in the future -- demonstrating an unusual "concern for operational security and a sensitivity to publicity."
"Chinese cyber espionage activity has demonstrated a higher tolerance for risk and is less constrained by diplomatic pressures than previously characterized," Mandiant added.
Pulse Secure parent company Ivanti has released patches and an integrity tool for users to check their builds for risk. It is recommended that the fixes are applied as soon as possible.
The US Cybersecurity and Infrastructure Security Agency (CISA) first issued an alert on the exploitation of Pulse Connect Secure products on April 21 and has since updated its guidance.
In other alerts this week, the FBI has warned of ongoing attacks using Fortinet/FortiOS vulnerabilities (CVE-2018-13379, CVE-2020-12812, FortiOS CVE-2019-5591). In May, an APT group managed to leverage these bugs to access a web server hosting a domain for a US municipal government.
Previous and related coverage
- Hacker leaks passwords for 900+ enterprise VPN servers
- Hackers are targeting flaws in these VPN devices now. Here's what you need to do
- DHS CISA: Companies are getting hacked even after patching Pulse Secure VPNs
Have a tip? Get in touch securely via WhatsApp | Signal at +447713 025 499, or over at Keybase: charlie0
Reassessing AI Investments: What The Correction In US Megacap Tech Stocks Signals
The recent correction in US megacap tech stocks, including giants like Nvidia, Tesla, Meta, and Alphabet, has sent rippl... Read more
AI Hype Meets Reality: Assessing The Impact Of Stock Declines On Future Tech Investments
Recent declines in the stock prices of major tech companies such as Nvidia, Tesla, Meta, and Alphabet have highlighted a... Read more
Technology Sector Fuels U.S. Economic Growth In Q2
The technology sector played a pivotal role in accelerating America's economic growth in the second quarter of 2024.The ... Read more
Tech Start-Ups Advised To Guard Against Foreign Investment Risks
The US National Counterintelligence and Security Center (NCSC) has advised American tech start-ups to be wary of foreign... Read more
Global IT Outage Threatens To Cost Insurers Billions
Largest disruption since 2017’s NotPetya malware attack highlights vulnerabilities.A recent global IT outage has cause... Read more
Global IT Outage Disrupts Airlines, Financial Services, And Media Groups
On Friday morning, a major IT outage caused widespread disruption across various sectors, including airlines, financial ... Read more

