Hades Ransomware Operators Are Hunting Big Game In The US
An unknown threat group is deploying a variant of Hades in targeted attacks against US big game.
On Friday, Accenture's Cyber Investigation & Forensic Response (CIFR) and Cyber Threat Intelligence (ACTI) teams published an analysis into the latest Hades campaign which has been operating since at least December 2020 until this month.
According to the cybersecurity researchers, at least three major companies have been successfully attacked with the ransomware strain including a transport & logistics company, a consumer products retailer, and a global manufacturer. Forward Air was reportedly a past victim.
Accenture says that the threat actors are focused on hunting organizations that generate at least $1 billion in annual revenue.
In the latest recorded attacks, the threat actors take a hands-on approach and use a mix of custom tools and fileless approaches.
Hades appears to infiltrate systems through internet-facing systems, Remote Desktop Protocol (RDP), or Virtual Private Network (VPN) setups using legitimate credentials -- which may be obtained through brute-force attacks or stolen data dumps.
Once Hades lands on a victim's machine, it creates a copy of itself and relaunches itself via the command line. The 'spare' copy is then deleted and an executable is unpacked in memory. A scan is then performed in local directories and network shares to find content to encrypt but each Hades sample secured uses a different extension.
A ransom note, "HOW-TO-DECRYPT-[extension].txt," is then dropped on the machine.
The ransomware notes obtained through Hades samples direct victims to install Tor and a unique address appears to be generated for each target. In total, six have been traced, which may indicate further infections.
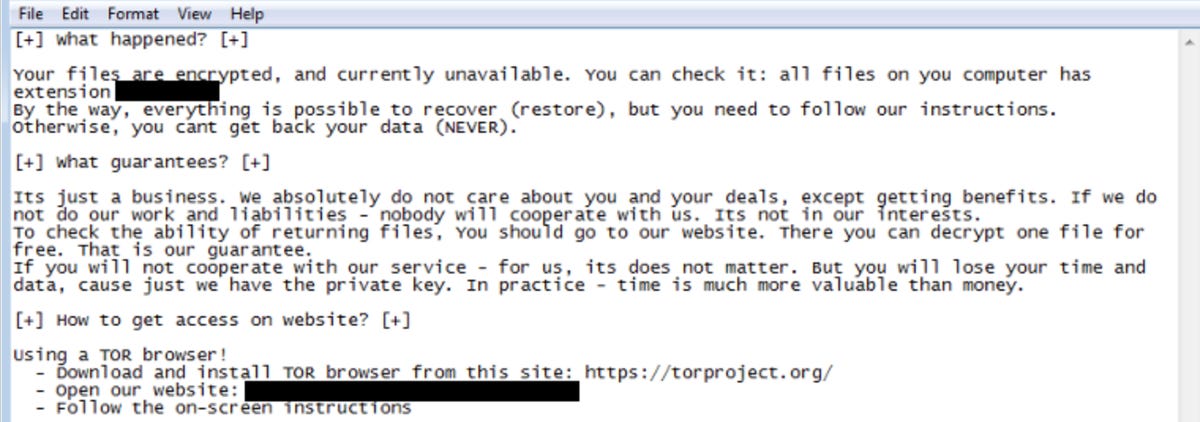
Similarities between ransom notes used by the Hades group and REvil ransomware operators. CrowdStrike considers Hades to be the successor to WastedLocker ransomware, a variant that has been deployed by REvil against US targets in past campaigns.
Cobalt Strike and Empire are used to manage command-and-control (C2) servers and to maintain persistence. Batch scripts, log clearance, disabling endpoint antivirus products, and modifying Group Policy Object (GPO) to disable audit logging are all implemented to circumvent existing defenses.
Hades also includes code obfuscation to avoid signature-based detection.
A variety of reconnaissance tools are also utilized to grab network, host, and domain information and to achieve lateral movement through networks.
"In addition, the threat actors operated out of the root of C:\ProgramData where several executables tied to the intrusion set were found," Accenture noted.
Prior to encryption, Hades operators steal and archive data before whisking it away to a C2 in what is known as a double-extortion tactic: pay up, or risk the leak of corporate data online.
"We assess with moderate confidence that the group's operations have just begun, and that Hades activity will likely continue to proliferate into the foreseeable future, impacting additional victims," Accenture says.
CIFR and ACTI have published Indicators of Compromise (IoC) for the threat group and Hades variant.
Previous and related coverage
- Ransomware attack halts production at IoT maker Sierra Wireless
- Purple Fox malware evolves to propagate across Windows machines
- Largest ransomware demand now stands at $30 million as crooks get bolder
Have a tip? Get in touch securely via WhatsApp | Signal at +447713 025 499, or over at Keybase: charlie0
Reassessing AI Investments: What The Correction In US Megacap Tech Stocks Signals
The recent correction in US megacap tech stocks, including giants like Nvidia, Tesla, Meta, and Alphabet, has sent rippl... Read more
AI Hype Meets Reality: Assessing The Impact Of Stock Declines On Future Tech Investments
Recent declines in the stock prices of major tech companies such as Nvidia, Tesla, Meta, and Alphabet have highlighted a... Read more
Technology Sector Fuels U.S. Economic Growth In Q2
The technology sector played a pivotal role in accelerating America's economic growth in the second quarter of 2024.The ... Read more
Tech Start-Ups Advised To Guard Against Foreign Investment Risks
The US National Counterintelligence and Security Center (NCSC) has advised American tech start-ups to be wary of foreign... Read more
Global IT Outage Threatens To Cost Insurers Billions
Largest disruption since 2017’s NotPetya malware attack highlights vulnerabilities.A recent global IT outage has cause... Read more
Global IT Outage Disrupts Airlines, Financial Services, And Media Groups
On Friday morning, a major IT outage caused widespread disruption across various sectors, including airlines, financial ... Read more

